In this section, we will go over some basic pen testing methods and some ways to keep your internet equipment safe from being exploited.
Below is what most SOHO’s (Small Office Home Office) look like. They consist of a box typically given by their ISP that acts as a switch, router, and WAP. This works for the most part but doesn’t really do a great job of protecting you from being exploited. One thing I noticed about probing ISP-given modems is they always respond to pings which from a hacker’s perspective, is a sign the device is up and there might be a vulnerability. You can have more control over what can be probed accessed with better equipment like Unifi, TP-Link, pfSense, and many others that offer higher security against possible attacks from WAN and LAN. More on this later.
When you access anything over the internet you are given a public IP address from your ISP. This public IP address is what all traffic on your network will be seen as over the public internet. If you were to open any ports for anything you want to access outside your home network, you could be at some serious risk. Using a tool called Nmap, you can scan your public IP address for any vulnerabilities, OS detection, and a whole lot more.
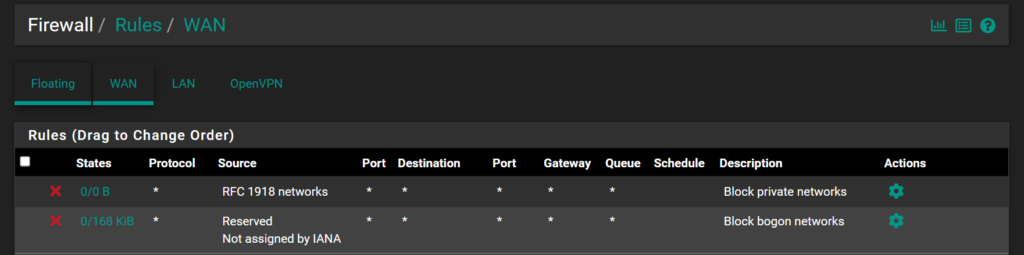
The main way you can be exploited is through the WAN. Making sure to harden your router is the first step in making sure you don’t get exploited. As shown below my router (pfSense) is blocking all incoming traffic through all ports and protocols. This is what you want when somebody is probing your IP from the outside internet; the first step is not being seen as easily.
Another way your network may be compromised is through devices on your LAN. IoT devices such as smart fridges, lightbulbs, etc… are mostly vulnerable. These devices may have their services they reach out to compromised and will be able to bypass your firewall even if you blocked all ports. It’s a good idea for these devices to put them on a VLAN (Virtual LAN). You can think of a VLAN as a virtual switch in a way. Devices on different VLANs cannot see or talk to each other. So you could put your trusted devices on for example VLAN 1 and your unsecured devices on VLAN 2 to avoid any communications between trusted and non-trusted devices. You could go a step forward and also enable Client Isolation, which is offered on some switch hardware.
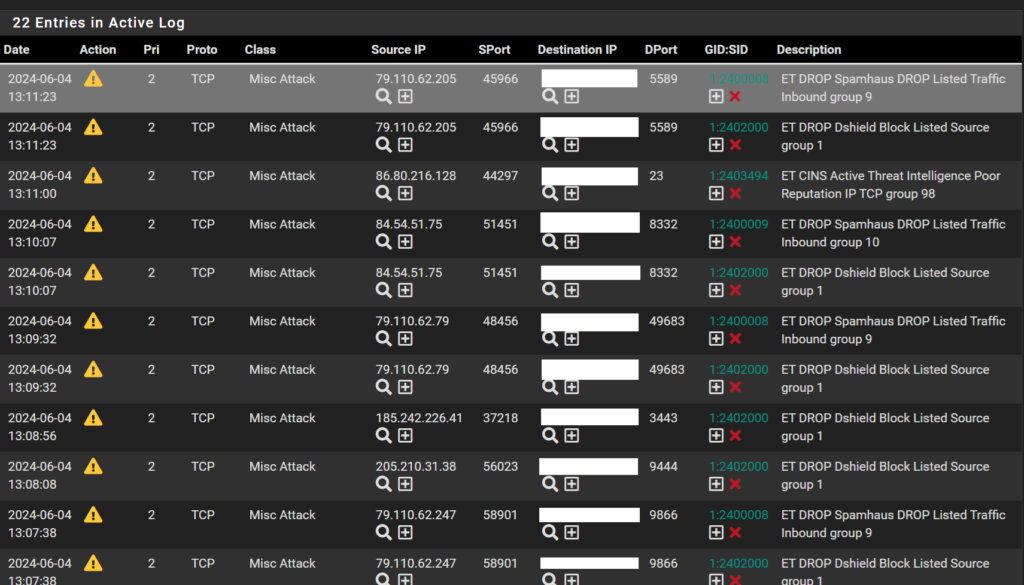
One way to be notified if a device is accessing a server or service that is malicious is by using a system called IPS/IDS (Intrusion Detection System / Intrusion Prevention System). Offered on more confiscated routers, this will give the user access to possible bad traffic flowing throughout the network. As shown below an IPS/IDS service called Snort analyzes packets and gives some info about what could be going on (my public IP hidden for privacy). In my case, I set up snort on the WAN interface but realistically you would be setting this service up on the LAN interface as if you configured everything correctly, the WAN should not be allowing any communication in.